Explained: How this Windows malware uses Google Translate and other programs to infect your PC/laptop – Times of India
Where is this malware hiding
Researchers have discovered some of the hiding spots of this malware. The blog mentions that one of them disguises itself as an “official Google Translate client.”. Users can do a Google search for the same through the Chrome browser (or other browsers with a Chromium-based framework). If you type “Google Translate Desktop download,” in the Google Search bar one of these malware campaigns will appear at the top of the search.
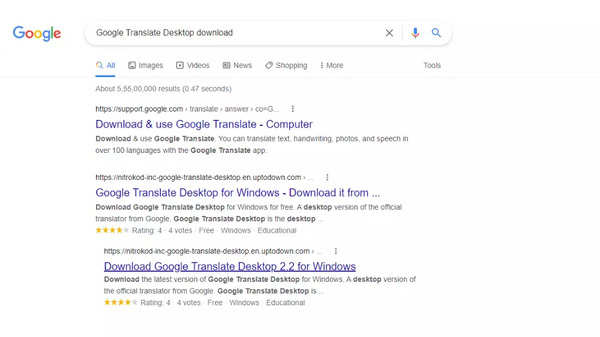
If you type “Google Translate Desktop download,” in the Google Search bar one of these malware campaigns will appear at the top of the search.
The blog also mentions that the malware is hidden within several real-looking apps listed on free software repositories like –Softpedia and is listed under the author name — Nitrokod Inc.
How is this malware different
The blog says that malware is first executed almost a month after the Nitrokod program (for example Google Translate) is installed. Moreover, the malware is delivered only after going through six stages of infection programs, the blog adds.
Apart from this, the infection chain keeps running for a long time using a scheduled task mechanism which gives the attackers time to remove the evidence, the blog notes. This makes it harder for users to detect the malware campaign.
The report also notes that the malware deploys multiple evasion techniques which include — delaying dangerous activity and establishing a firewall exclusion — the crypto-miner can easily conduct its business without raising any alarms.
Moreover, the report also warns that the campaign has been around for a long time and some of the “rigged programs” have been downloaded by more than 100,000 people.
How these infection programs can be a problem
According to a report by TechRadar, crypto mining malware is usually not designed to steal data or encrypt files — like ransomware, however, an infection can cause different kinds of issues for the victims.
Apart from affecting the performance of the device, these infections can also drive a material increase in energy consumption as CPU resources are set aside for mining activity, the report suggests. This can increase consumer bills and affect users financially as well.
How to avoid the malware campaign
To stay safe from such unwanted malware campaigns internet users are recommended to download apps exclusively from authentic marketplaces like — Google Play or the Windows Store. The report mentions that some strains can hide from built-in security services, and an external antivirus system might help detect an infection.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.
