Okta’s Security Center opens window to customer insights, including threats and friction
Since acquiring the application team platform Auth0 in 2001, identity management company Okta has pursued a platform-neutral strategy for both internal and external consumer identity authentication that includes delivering insights to IT teams overseeing security and identity-based access protocols.
The 14-year-old company and single sign-on market share leader announced this month that it is adding a key element of visibility, the Security Center, to its Auth0-powered Okta Customer Identity Cloud.
Jump to:
Offering wide visibility of authentication activity
The Security Center dashboard is designed to give near real-time asset visibility to teams focused on customer identity, user experience and security. The Security Center serves up authentication events, security incidents and user experience at points, particularly where security friction could make or break the consumer interface experience, according to Okta (Figure A).
Figure A
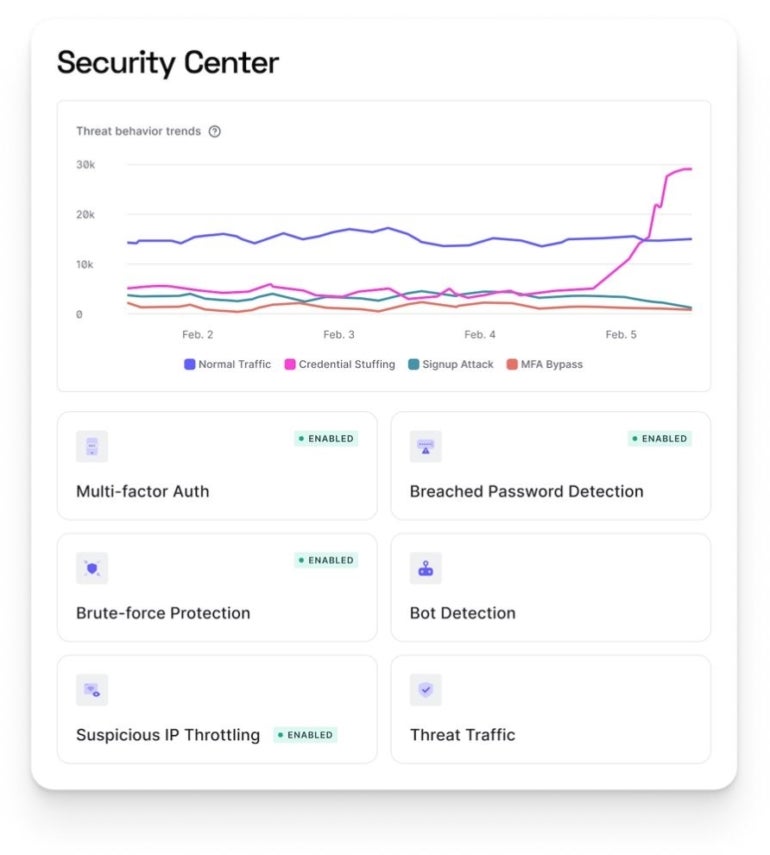
Ian Hassard, senior director of project management at Okta, said that, going forward, every Okta enterprise customer will have Security Center access whether they have the company’s attack protection product or not
Addressing identity and sign-on management challenges
Hassard explained that, while Okta’s technologies serve both internal employees and external-facing identity interfaces, the latter environment presents special challenges.
“In the customer identity world, we’re talking about 10 million or 50 million users, which means sorting through a lot of the noise and trying to surface attack insights, which are a little hard for somebody who’s not living and breathing customer identity,” Hassard said.
SEE: How one company is using artificial intelligence for two-factor authentication (TechRepublic)
Using insights to parse attack veracity
The company said the security dashboard grabs data from Okta Customer Identity Cloud to provide a window into real-time authentication events, potential security incidents and threat response efficacy as well as the current state of attack protection and authentication traffic.
“To understand what is or isn’t an attack, we’re able to analyze the patterns across logins,” said Hassard. “This means that when we see an attack or when a customer confirms that there’s an attack, we’re able to have the collective shared intelligence of what that actor was doing and what — in this context — ‘bad’ looks like.”
Platform agnostic, behind the scenes
At the RSA conference earlier this month Jameeka Aaron, chief information security officer of customer identity at Okta, explained to TechRepublic that the company’s strategic position in the identity ecosystem is to be platform agnostic and a silent partner. “One of the biggest you’ve never seen.”
Aaron said Okta’s larger strategy is platform agnostic, with a partnership focus on identity management.
“We want to make it really easy to connect your applications to Okta, so our neutrality is one of our biggest superpowers,” Aaron said.
“I came from the retail and manufacturing space, and one thing we always knew is that the customer decides. What we are trying to do is allow businesses, our customers, to decide what tools they want and deploy them,” she added. “So, for example, if you use [Cisco’s] Duo, you can also use Okta for single sign-on, enabling one login to access many applications. And, if, say, 1Password is your password vault, you can plug that into Okta as well.
“We think of other companies in the identity space as partners, so we remain platform-agnostic as much as we can, so the choice is still with the company.”
SEE: Passwords are a thing of the past … almost (TechRepublic)
Finding the Goldilocks zone for security friction
According to Okta, the Security Center interface allows for fine-tuning of an enterprise’s attack protection strategy by showing how multifactor authentication, rate limiting and CAPTCHA affect their applications.
Hassard said data on customer engagement with sign-on interfaces is an important customer retention insight that allows identity management teams to tweak security friction without compromising protections against identity exploits.
“Being able to provide those insights in real time has a lot of value,” said Hassard. “For example, if you’re a bank and you’re using our platform, you may well increase security friction because your customers appreciate the importance of security for preventing fraud.
“But if you’re buying something at a retail app that you can purchase from five other apps, you are going to pick the one that has the best UX, so that app may want to dial back friction toward convenience.”
A 2023 study by the Baymard Institute, reporting an average 69.99% shopping cart abandonment rate derived from 48 e-commerce studies, said 17% of those abandonments were due to an overly complicated, lengthy checkout process.
Hassard said with the unique nature of end-user identity and the variable nature of its challenges — depending on the user, the market, the type of application customers are running — there is no one-stop-shop in the conventional tools domain for visualizing customer identity.
“It’s too niche of a problem space for most of those players,” said Hassard. “So, that’s where we’re coming in and saying, ‘Look, we’re going to give you the insights that we think are necessary to understand what an attack looks like.’”
Auth0 for workforce identity
Aaron said that, on the workforce side of the business, Okta will release an Auth0-powered tool for its ThreatInsight workforce identity service, offering a longitudinal view of threat surfaces associated with identity access management.
“ThreatInsight will essentially give customers the risk signals that we see and use, which helps them make critical decisions,” said Aaron.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.
