LastPass hacked: How to export and protect your passwords
LastPass is no stranger to data breaches. It’s suffered several high-profile leaks, with the most recent (and alarming) incident happening just last year. When news first broke in August, the developer assured everyone that customers were unaffected. But in a complete reversal, the company’s December updates were grim—customer data had been taken after all.
If you’re feeling like you want to leave the service, you can hardly be blamed. In this latest breach, not only was personally identifying information like billing addresses, telephone numbers, and IP addresses stolen, but vault data as well. Most damning: Some of that vault data was unencrypted.
The good news is that exporting your data is quick and relatively straightforward. You get the entire vault in a single file that you can then use to upload to a new password manager.
Here’s how to export your passwords from LastPass—and how to do securely. Plus, what you should do afterward to ensure the safety of all your online accounts.
How to export your LastPass passwords
Getting your passwords out of LastPass is actually very easy. More complicated is ensuring the exported file remains secure. LastPass exports in either CSV and XML file formats, and those file types aren’t encrypted.
You don’t want your passwords downloaded as plain text—even if you delete the file, it can be recoverable on an unencrypted drive. And many people haven’t encrypted the drives on their PC.
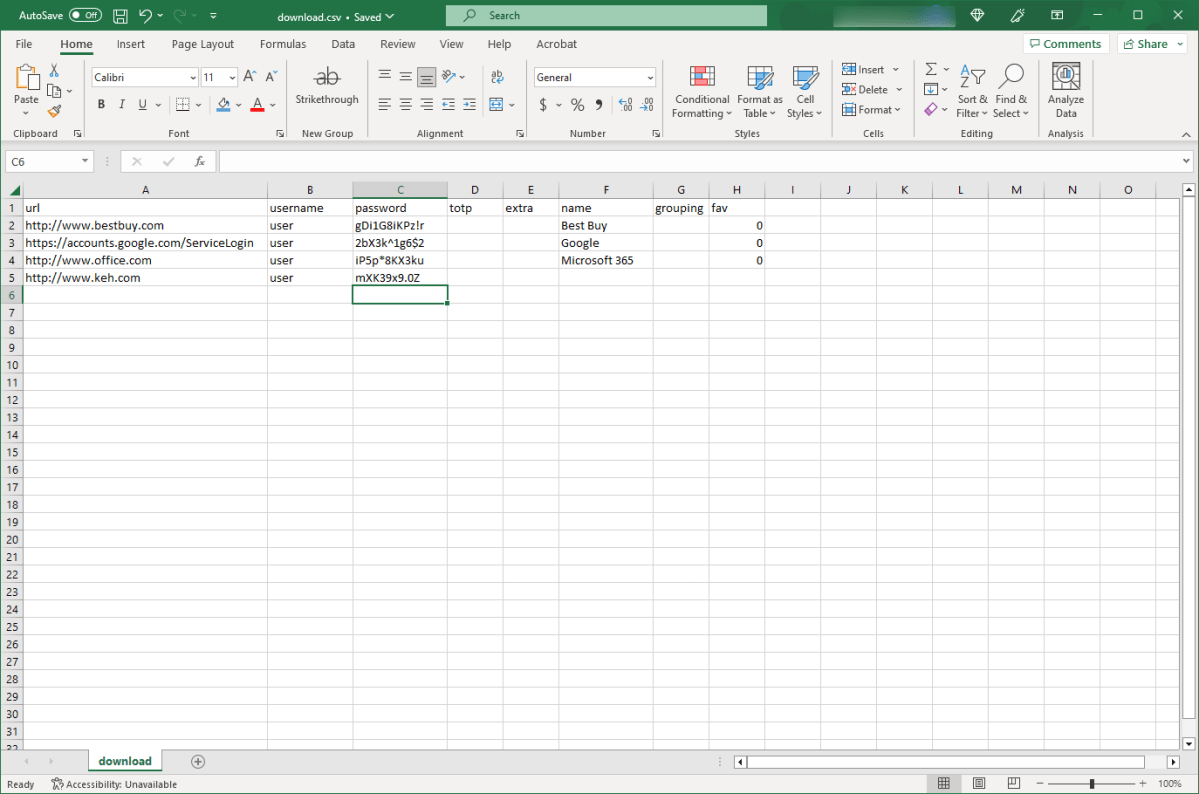
Your exported data from LastPass will be saved to an unencrypted file. (A sample CSV document is pictured here).
PCWorld
The less complex method is to download the file to a drive fully encrypted by Windows, then permanently deleting it as soon as you’re done importing your info elsewhere. (Leaving it in the Recycling Bin means the file is available and unencrypted whenever you’re logged into your computer.) This is not a bulletproof method, as you can recover the data while logged into your PC, but it’s a decent middle ground.
If you can tolerate a little more effort, I recommend creating an encrypted folder using VeraCrypt, then downloading exported vault data to that location. It acts like a safe for the file. Your data only becomes available when the container is unlocked. When you’re done, just delete the whole set while locked; if the container’s password is never shared, the valuable info inside should remain secure.
Once you have your security precautions set, follow these steps to get your data out of LastPass, either via the web interface or the browser extension.
Note: If you’re using a free account that’s tied to mobile devices only, you should be able to export via the web. If not, a workaround is to start a paid trial, so that you temporarily get multidevice access.
How to export from LastPass via the browser extension
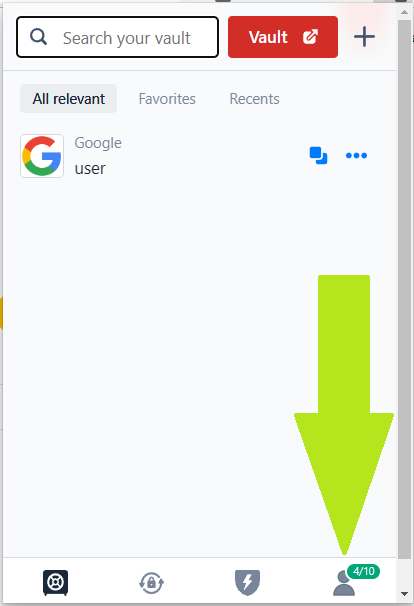
Step 1: Access your account settings
PCWorld
- Open the browser extension, then click on the account icon.
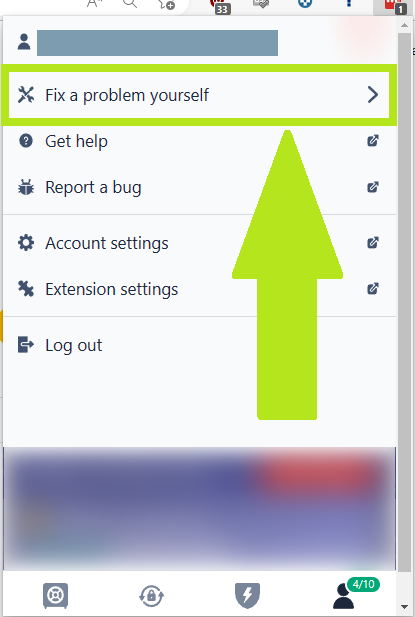
Step 2: Dig into the “Fix a problem” menu options
PCWorld
- Choose Fix a problem yourself.
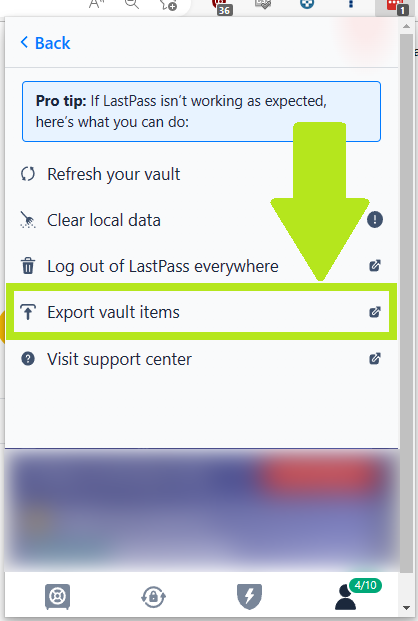
Step 3: Export your vault items
PCWorld
- Click on Export vault items. Your file will immediately begin downloading.
Reminder: The downloaded file will be in an unencrypted format. Anyone with access to the file can see all of your passwords. For a secure way to download the file, see the notes at the start of this section.
Your file can now be imported into a new password manager (either another cloud-based service or software installed to your computer). The process should be straightforward, but if you run into any issues, you can look up your new service’s help pages for instructions.
How to export from LastPass via the web interface
Step 1: Access the Advanced Options
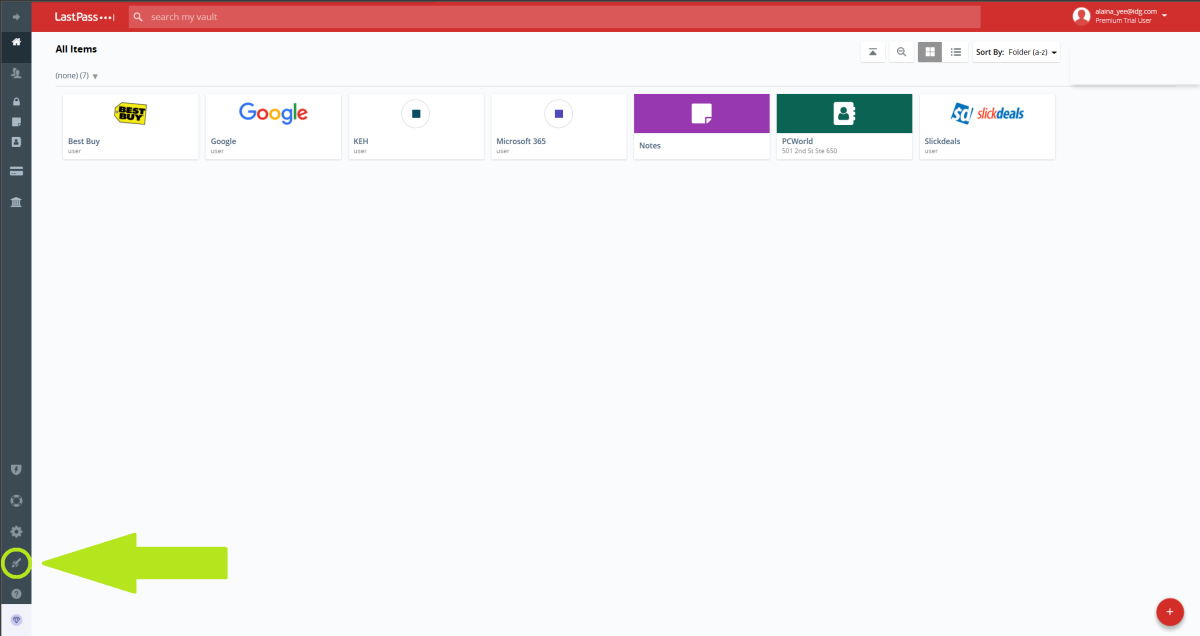
PCWorld
- In the left nav bar, click on the icon for Advanced Options. It should be the second from the bottom.
Step 2: Choose Export
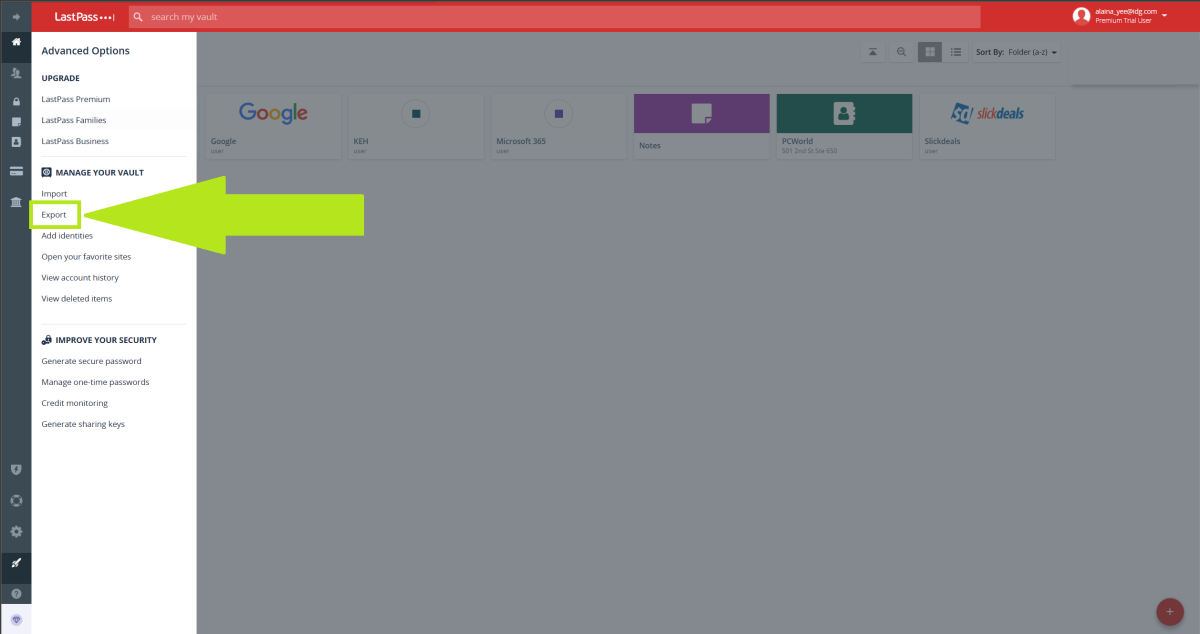
PCWorld
- Under Manage Your Vault, choose Export. A green banner will pop up at the top of the page, instructing you to check your email.
Step 3: Verify the export request
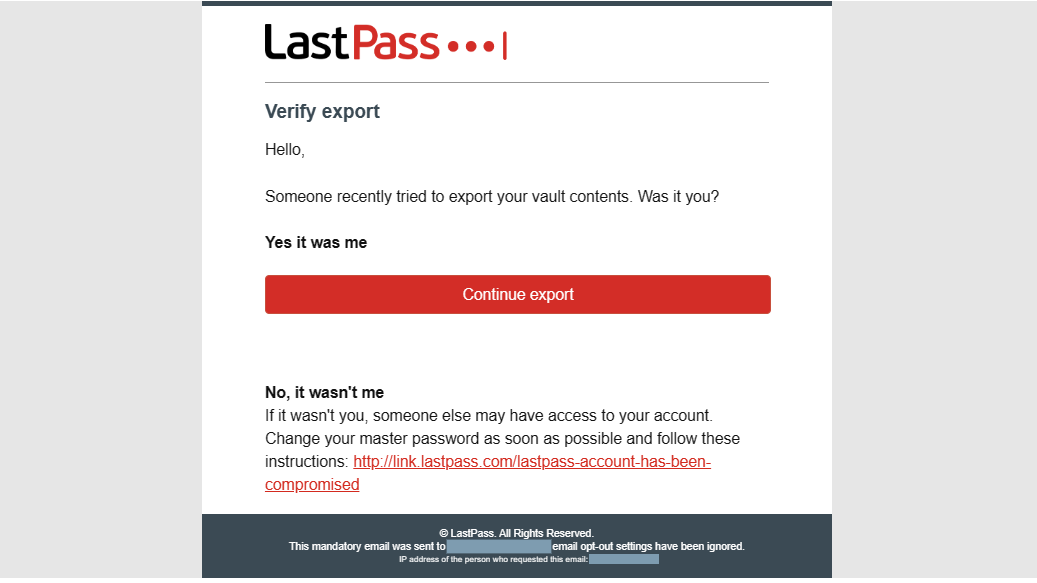
PCWorld
- Log into the email address associated with your account. Open the email from LastPass and click on the Continue export link within. A browser tab should open, saying that the export is ready.
Step 4: Enter your login info to begin download
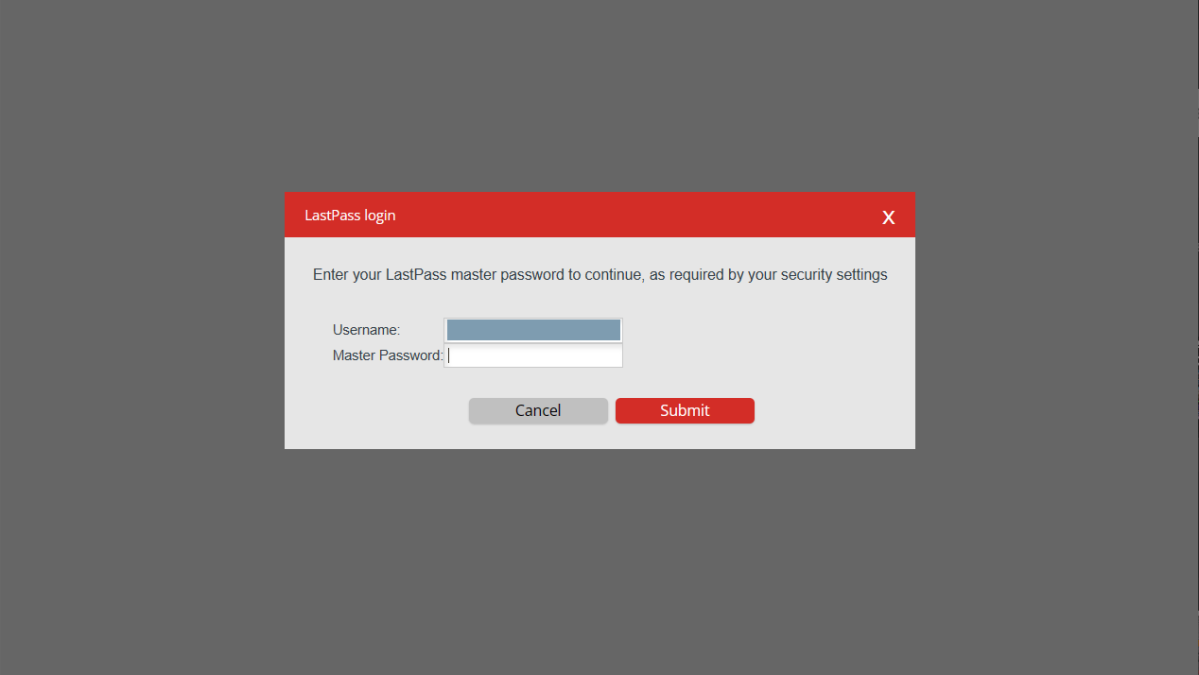
PCWorld
- Go back to Advanced Options > Export. To begin the download, enter your user name and password.
Reminder: The downloaded file will be in an unencrypted format. Anyone with access to the file can see all of your passwords. For a secure way to download the file, see the notes at the start of this section.
You can now import this file into a new password manager (be it another cloud-based service or a piece of software installed to your computer). It should be a straightforward process, but if you run into difficulties, your new service should have help pages with instructions.
You’re not done yet, unfortunately
Usually, leaving a password manager for another one is simple. You export your passwords from the old service, import the info into your new service, and then go back to your life.
Ditching LastPass because of its breach makes matters more complicated. Because hackers have your vault data, your master password is the only thing standing between them and access to your accounts. To ensure your security, you’re best off changing the passwords in your vault.
Hopefully you had a strong random master password, which will make brute forcing entry into the vault very difficult. But there’s no way around this one if you want to be sure you’re safe. You can’t change your LastPass master password and be done—the vault data captured is linked to the master password you had at the time of the hack. Updating it now won’t help.

istockphoto.com/ManuelSousa
With hundreds of passwords a part of our daily lives, this task is no quick feat. Our recommendation? Work in graduated steps:
- Move to the new password manager
- Immediately change all of the passwords for critical services—banks and other financial institutions, tax preparation, government programs, etc. Anything that could be ruinous if someone got hold of those accounts.
- Work your way through the remainder of your passwords, starting with those that have more sensitive info stored (i.e., physical addresses, birth dates, credit card numbers). Now’s a good time to also wipe that info from websites; keep it in your password manager instead.
You want to do this after you leave LastPass, especially if you’re concerned about remaining security vulnerabilities the company has yet to detect. This breach is not LastPass’s first—and given the company’s history, likely not its last, either.
(Whether LastPass is that much better at transparency, has that much more difficulty maintaining security, or is just a bigger target in general is a question to be answered another time.)
Whatever you do, don’t abandon password managers all together. Security online is imperfect, and so the solutions for it are also imperfect—but some systems are much more flawed than others. Reusing passwords, using weaker passwords, writing them down in a notebook—these won’t keep you safe. You can find a good password manager (and a system of use) that works for you.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.
