Cisco Talos Reports Microsoft Windows Policy Loophole Being Exploited by Threat Actor

Cisco Talos discovered a new Microsoft Windows policy loophole that allows a threat actor to sign malicious kernel-mode drivers executed by the operating system. The threat actor takes advantage of a specific compatibility policy from Microsoft to enable the signing of malicious kernel-mode drivers. Then, the RedDriver malware, which might be developed by a Chinese-speaking threat actor, targets browsers used primarily in China.
Malicious kernel-mode drivers represent a severe threat as opposed to user-mode drivers. Learn more about these drivers, what RedDriver malware does and who is targeted, and how to keep your business safe.
Jump to:
Why malicious kernel-mode drivers are a severe threat
Microsoft Windows operating systems handle two kinds of drivers: user-mode drivers and kernel-mode drivers. The latter are much more powerful than the user-mode drivers for multiple reasons. Kernel-mode drivers:
- Run at a low level in the operating system, making them harder to detect than user-mode applications and allowing the execution of code with the highest privileges.
- Can remain persistent, being executed every time the operating system starts.
- Can be used to bypass security because they have direct access to hardware and system components, such as firewalls or antimalware software.
- Can embed rootkit functionalities to hide their presence or the presence of other software such as malware on the system.
Microsoft has deployed measures to protect systems and fight the threat of malicious kernel-mode drivers based on certificates. Kernel-mode drivers need to be digitally signed with a certificate coming from a verified certificate authority. From Windows 10 version 1607 on, Microsoft updated the signing policy to no longer allow new kernel-mode drivers that have not been submitted to and signed by its Developer Portal.
The loophole that is being exploited
In order to maintain the functionality and compatibility of older drivers, Microsoft created a few exceptions for the following cases:
- The computer was upgraded from an earlier release of Windows to Windows 10 version 1607.
- The secure boot parameter is set to off in the computer’s BIOS or UEFI firmware.
- Drivers signed with an end-entity certificate issued prior to July 29, 2015 that chains to a supported cross-signed Certificate Authority.
A loophole exists here in the way a newly compiled driver can be “signed with non-revoked certificates issued prior or expired before July 29th 2015, provided that the certificate chains to a supported cross-signed CA,” as written by Cisco Talos.
Therefore, multiple open-source tools have started exploiting this loophole to enable developers to sign drivers successfully.
Tools exist to help developers exploit this Windows policy loophole; Cisco Talos mentions Fu**CertVerifyTimeValidity (actual name is in the Cisco Talos report) and HookSignTool, both of which are available for free on the internet (Figure A). Fu**CertVerifyTimeValidity has been available since 2018 on Chinese forums, while HookSignTool appeared in 2019.
Figure A
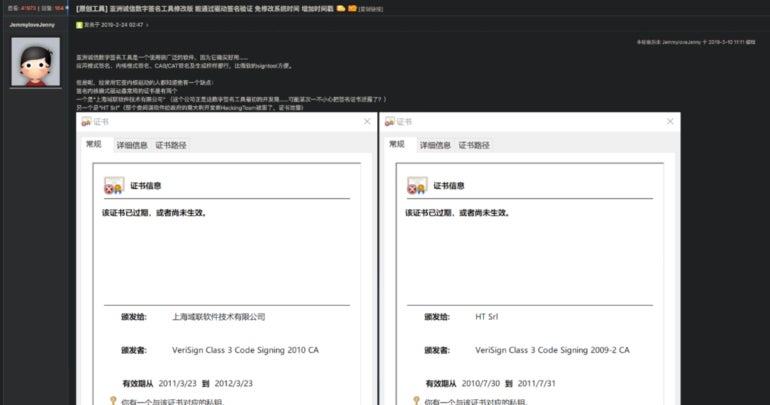
Those tools use the Microsoft Detours package, which was made for monitoring and instrumenting API calls on Windows, to pass a custom time in the “pTimeToVerify” parameter, allowing an invalid time to be verified. Detour is also used to change the signing timestamp during execution.
Both tools need a non-revoked code signing certificate that expired or was issued before July 29, 2015 and its private key and password to successfully forge a digital signature. Cisco Talos researchers found a file hosted on GitHub in a fork of one of the tools containing more than a dozen expired code-signing certificates frequently used with both tools.
Meet RedDriver malware
The attack chain starts with a single executable file named DnfClientShell32.exe that injects a DnfClient resource into a remote process. Then, DnfClient starts communicating with the threat actor’s command and control server (C2) to initiate the download of the RedDriver payload. DnfClient also opens a listening port on localhost (127.0.0.1).
According to Cisco Talos, RedDriver is an undocumented malicious kernel-mode driver whose name comes from the binary itself, as its developer named it in the compilation project file path. RedDriver has been signed using the HookSignTool. Cisco Talos researchers found different versions of the malicious kernel signed with different certificates.
RedDriver, once executed, allows browser hijacking based on a hardcoded list of browsers, many of which are popular in China (Figure B). And, it adds a root certificate to the system.
Figure B
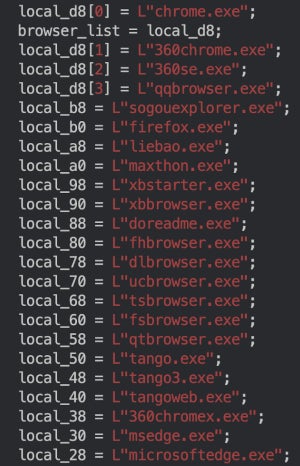
RedDriver redirects traffic from those browsers to 127.0.0.1, yet it is unclear why. It still represents a high threat as RedDriver is able to manipulate browser traffic at the packet level by using the Windows Filtering Platform, which is a set of APIs and system services that provides a platform for creating network filtering applications.
An earlier version of RedDriver was found by Cisco Talos researchers. That version has been active since at least 2021 and contained a hardcoded list of names belonging to dozens of drivers, “many of which pertained to software that is Chinese in origin” and “focused on software that would be used in Internet cafes” according to Cisco Talos, which also mentions that the targeting of internet cafes in China by cybercrime groups is not unusual.
Chinese-speaking threat actors and victims
The developers of RedDriver have left a number of traces indicating they are Chinese-speaking individuals.
For instance, all domains associated with RedDriver have been located in China. The RedDriver operation involves code from multiple open-source tools mostly originating from Chinese-speaking forums. An initial portion of the RedDriver code was originally posted on a Chinese forum.
Just as the RedDriver threat actor is probably of Chinese origin, the targets of RedDriver are Chinese-speaking people. The list of targeted browsers and the list of driver names targeted by RedDriver are mostly related to Chinese software. The initial infection files starting with “Dnf” are likely an attempt to masquerade as a highly popular game in China, Dungeon Fighter Online, referred to as DNF.
How to protect your business from this cybersecurity threat
Cisco Talos reported all the certificates used by the threat actor to Microsoft. A drivers block list maintained within Windows by Microsoft has been updated to block all those certificates.
Cisco Talos’s research does not indicate the initial method used to infect computers, which might be website compromise, phishing emails or other social engineering techniques, so general cybersecurity hygiene needs to be deployed.
For starters, all operating systems, firmware and software need to always be up to date and patched. This will avoid being compromised by common vulnerabilities.
Security solutions need to be deployed to monitor endpoints and networks for any suspicious behavior. Attached files in emails should be carefully analyzed.
Finally, employees should be trained to detect fraud and infection attempts, especially phishing.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.
